On June 17, 1950, the seven members of the Arab League signed the modern Middle East’s first collective security pact: the Treaty of Joint Defense and Economic Cooperation. The alliance was a failure. It never brought the Arab militaries together into an effective, combined force. It struggled to deter, let alone combat, threats. Israel decisively defeated its members in 1967, then again during the War of Attrition and the October War. Even worse, Egypt and then Jordan signed separate peace treaties with Jerusalem despite threats of alliance expulsion. The pact did little to temper the Arab Cold War, and, indeed, members regularly coerced or even attacked one another, as with the 1990 Iraqi conquest of Kuwait and opposing Saudi and Egyptian interventions during the North Yemen Civil War.
In many ways, this treaty was designed to fail. Its strategy was wholly unsuited to its members. Composed of small and weak countries, none had advanced military capabilities, modern and diversified economies, nor even significant diplomatic influence. The league could not consolidate its diverse forces and national commands, and, even before signing, members recognized that they lacked the political cohesion required for combined military planning and operations.
Yet they directly emulated NATO’s design. Despite internecine conflict, the league founded an integrated command structure—the United Arab Command—modeled on NATO’s Supreme Headquarters Allied Powers Europe. Despite limited trade and economic ties, the treaty established an Economic Council to coordinate member industry and agriculture, much like Article 2 of the North Atlantic Treaty encourages. Most importantly, the pact copied NATO’s Article 5 defense guarantee, stating that signatories “consider any [act of] armed aggression made against any one or more of them or their armed forces, to be directed against them all.” Despite wide differences in member characteristics, geostrategic threats, and economic conditions, both Western Europe and the Arab League pursued identical alliance strategies.
We see this same pattern of strategic convergence on infertile ground across history. In 1833, two small Italian city-states signed a defense pact modeled after the Quadruple Alliance (1815), the preeminent pact of its time. Similarly, in 1864, Colombia and Ecuador concluded a defense partnership. Like the Quadruple and Italian alliances, it stipulated the exact number of naval forces each party would provide in a conflict. But neither had a functioning navy at signing. Indeed, Colombia had decommissioned its naval school and abolished the Ministry of the Navy almost forty years before.1 Prior to World War 1, nearly all alliances were secret. Since then, secret pacts form a negligible, at times nonexistent, part of the global alliance network.2
Interstate military alliances are central to international security. They deter conflict, aggregate power to challenge adversaries, underpin regional and global order, and foster security communities that create durable, peaceful relations among countries. These pacts have also spread wars across continents and dragged states into conflicts they would have rather avoided, generating new bloodshed. Given these stakes, nations have powerful incentives to get their alliances right. Overcommitting risks entrapment, but institutionalized coordination can offer more robust and durable cooperation. Limited treaties offer diplomatic flexibility, but raise the risk of abandonment by partners at critical and inopportune moments.
To make effective pacts, countries adopt specific alliance strategies: Means-ends beliefs about the guarantees, political promises, and organizational features that best allow their partnerships to overcome cooperation problems and generate military security. States deterring threats publicly announce defensive obligations. Allies hoping to conquer neighbors spell out the division of spoils, cost-sharing formulas, and troop contributions. States facing domestic or international resistance to their security cooperation keep their pacts secret. Nations “mix and match” these features to address the specific threats, domestic constraints, and military capabilities they face. Given the range of these factors, states should carefully tailor their military partnerships. We expect wide variation in alliance strategy, organizational design, and military guarantees.
This expectation is wrong. The examples above are not isolated coincidences. In any given year, 75 percent of states pursue the same alliance security strategy. They provide similar guarantees, create similar internal coordinating mechanisms, and use alliances to achieve similar foreign policy goals. Countries converge on a single, legitimate approach to create security through military pacts: a dominant alliance strategy or form. Across periods divided by major wars, this form varies sharply. In some, it features a realpolitik approach to military cooperation emphasizing fluid realignment and alliance abandonment. In others, it fosters integrative, cohesive, and institutionalized security communities. Within those periods, however, the dominant strategy’s prevalence locks in a single conception of legitimate and credible alliance cooperation. It thus constitutes an integral component of international order, defining broad swaths of diplomatic history, as well as structuring and constraining military policy, strategic alignment, and the likelihood of war for decades.
This book asks: What causes the dominant alliance strategy? What spreads it? And what effects does its variation have on international security and order? Its answer is grounded in major war. As Ikenberry (2001) notes, a single great power emerges victorious from these global conflicts. Its decisive, comprehensive victory grants a windfall of power and authority. This new hegemon then creates a core alliance gathering other great but lesser powers to meet its most important security challenge in the postwar strategic environment. This central pact forms the nucleus of the dominant strategy.
The leading state does not impose this form on secondary and peripheral states. Indeed, it actively avoids doing so. But such countries draw their own lessons from the new global leader. They elevate the core alliance as the standard of credible and legitimate military cooperation. Emulation—the diffusion of a single alliance strategy—proceeds according to two paths. Secondary countries—those allied to a core alliance member—follow a credibility diffusion process. Because their partners have a guarantee from the hegemon, these states worry about “relative reliability”: the rank or prioritization of their pact within their partner’s broader alliance portfolio. In essence, they ask: “What are the limits of my ally’s commitment, and how can I ensure my pact stands above or at least equal to its competing obligations?” They push partners to emulate the core alliance’s strategy and features in their own separate pacts.
Peripheral countries—allied nations not connected to either core or secondary states—emulate to gain status benefits. Mimicking the central alliance strategy reinforces the sovereign status of these states, demonstrating that they abide by the outward markers of effective alliances and pursue foreign policy goals validated by the hegemon. In so doing, peripheral nations hope to bolster their internal and external legitimacy, raising their standing within the international system. In total, the dominant form subverts theoretical expectations. Instead of tailored pacts designed according to means-ends utility maximization, states ignore their individuated conditions and coalesce on a single alliance strategy.
This chapter establishes the phenomenon of interest. Using the Alliance Treaty Obligations and Provisions (ATOP) dataset, section 1.3 demonstrates that most alliances converge on a single design. Few states—and none of the great powers—defy this dominant alliance strategy in their formal military partnerships. Existing scholarship provides little analytical traction over the dominant form’s existence and variation, although section 1.4 outlines two possible explanations. If enough states face the same security challenges, these common threats could produce institutional isomorphism. Alternatively, hegemons could impose their preferred designs. Substantial empirical and theoretical problems confront both approaches. Consequently, the following chapter will introduce a new theory drawing upon network analysis and social theories of rank and status to explain the book’s puzzle, the dominant alliance strategy. Finally, section 1.5 will outline how the book is organized.
Far more structure emerges from major wars than we suspect. Security regimes are not driven solely by hegemonic or great power actions but also by decisions from multiple strata in the interstate system. These decisions, moreover, follow their own, separate logics, with states responding to a mix of power, credibility, and status incentives depending on their network position. A complex, interactive process generates more uniform security behavior and international order than previously understood.
This project defines alliances as: “Written agreements, signed by official representatives of at least two independent states, that include promises to aid a partner in the event of military conflict, to remain neutral in the event of conflict, to refrain from military conflict with one another, or to consult/cooperate in the event of international crises that create a potential for military conflict.”3 Within this definition, states can choose from a wide variety of alliance design features and functional roles to facilitate cooperation, account for individual member vulnerabilities or liabilities, settle intra-allied disagreements, and more effectively deter threats. Together, these design choices create an alliance security strategy: A means-ends mapping or belief about how particular military guarantees, organizational features, and political commitments (i.e., means) can be applied in alliances (i.e., ways) to allow cooperation, bolster cohesion, and, ultimately, generate security (i.e., ends).
The literature on alliances has grappled with many of these design elements, grouped into three broad categories: alliances’ functional roles or purposes, their management, and their cohesion. Prior studies generally adopt a functionalistrationalist approach: States select particular design features because they believe they will effectively resolve specific cooperation problems. For example, with respect to the functional purposes of alliances, defensive realists expect most countries to form defensive military agreements targeting specific threats.4 Weitsman (2004)’s seminal alliance typology argues that high external threats prompt states to have clearly defined military obligations and conditions for activation. By contrast, Benson (2012) and Kim (2011) argue that entrapment fears spur partners to adopt conditional or ambiguous security guarantees, the better for a state to constrain adventurous or risk-taking behavior by an ally. Pacts should therefore include clear limits on the casus foederis (i.e., events triggering the military commitment); be very little thinly institutionalized, if at all; and primarily commit states to mutual consultation and possibly defense. Abandonment should also be quite common.5
Although sharing many predictions with their defensive counterparts, offensive realists might expect somewhat more offensive and neutrality pacts, particularly as rising powers attempt to establish regional or even global hegemony. To seize strategic surprise, these pacts may be secret. To address distributive conflicts among partners, these alliances may agree to specific divisions of spoils and/or conquered territory in advance. In either case, both forms of realism anticipate a realpolitik approach to alliance strategy. As threats and capabilities increase, states create sharply delimited alliances to either defend or advance specific national interests, as well as fluidly rebalance against emerging adversaries (including former allies).
Other studies follow Koremenos et al. (2001) in exploring how states use certain provisions to overcome management problems. Wallander and Keohane (1999) and Wallander (2000) claim that nonmilitary coordinating institutions, larger membership size, and longer expected duration are responses to high issue density and policy spillover. States establish coordinating mechanisms with broad delegated portfolios to develop comprehensive policies and avoid duplication of effort. Bearce et al. (2006) show how states use information-sharing provisions to mitigate crisis escalation, while Ikenberry (2001) and Schroeder (1976) highlight institutional binding as a way to manage imbalances of power and policy coordination among allies. Finally in this area, Bensahel (2007) and Moeller (2016) explore alliance warfighting performance, how elements like unified command structures, equipment interoperability, common doctrine, and joint training can act as force multipliers and contribute to battlefield success and military victory or defeat. Insofar as security partners face, say, high interdependence causing spillover or threats requiring significant multilateral coordination, they have a wide range of institutional strategies and options to address these concerns.
The third category includes alliance strategies to handle cohesion and credibility problems. States can leverage reputations of resolve to facilitate alliance-making, while institutionalization can help countries that have previously reneged on their commitments find new partners.6 Gibler (1996) explores alliances that settle territorial disputes, which typically contain detailed provisions demarcating land to be exchanged and national borders. Lake (2009) and the small states literature examine asymmetric obligations in partnerships between powerful and peripheral countries.7 The latter can offer few security benefits to the former, and so instead exchange political acquiescence for military assistance. Even outside of patron-client relations, distributional conflicts over burden-sharing can prompt member-specific contributions.8
Under certain conditions, states may want to reduce their credibility and alliance cohesion. Domestic political costs and the strategic benefits of flexibility may lead states to limit institutionalization and other markers of commitment.9 Gibbs (1995) finds that those same incentives lead states to include secret provisions or enact completely hidden pacts. Democracies can rely on costly ratification procedures and securing the support of veto actors to demonstrate commitment, obviating institutionalization.10
The choice of alliance strategy has critical effects on interstate security and global stability. Ikenberry (2001) places institutionalized alliances at the heart of constitutional international orders. By contrast, fluid, “realist” pacts may spur and spread warfare,11 although others highlight the role of carefully worded guarantees to prevent this from happening.12 Military coordination should increase the likelihood of victory, while information-sharing provisions reduce intra-allied conflict and stabilize security relations.13 At the limit, certain alliance strategies can foster security communities where war is unthinkable between members.
All these theories expect states to carefully tailor their pacts to specific threats, constraints, and capabilities. Partners should “mix and match” features to optimize the security their alliances produce. For example, a country facing a powerful threat but suffering reputational problems might ask for defensive commitments, coupled with explicit conditions on invocation, consultative fora, and clear decision-making procedures to address concerns about reliability. Those working with potentially untrustworthy counterparts to acquire territory may create offensive or neutrality pacts that commit partners to specific spheres of influence or areas of conquest in advance. Certain design choices might be more “popular” than others, but such “popularity” typically reflects a higher prevalence of underlying causes. For instance, advances in transportation and communications technology make it easier for alliances to establish management bodies. In addition, some features may correlate with others. Offensive realism might expect states to adopt a common set of designs in their alliance strategy: neutrality and offensive obligations, minimal institutionalization, perhaps also secrecy, provisions clearly dividing gains, and/or delineated contributions. But this would only apply to a select set of states embarking on aggressive expansion or regional hegemony. Their targets would likely adopt opposing features (e.g., defensive guarantees with robust institutionalization), preserving variation in partnership design. Given the range of individuated state challenges, threats, vulnerabilities, and capabilities, the literature would expect diversity in alliance security strategies.
This expectation is wrong. Alliance characteristics move and disappear from the international security system as blocks. Design choices are strongly correlated, such that analyzing features individually misses broad, transhistorical patterns. Most importantly, rather than diversity, the majority of states and pacts ignore their individuated circumstances and converge on a unique, prevailing alliance strategy with a single set of cooperative functions, normative expectations, and organizational traits. This dominant alliance strategy or form is not a mixed bundle of what features happen to be widespread at a given time. These features conceptually—and as discussed in the next chapter—theoretically connected through normative beliefs about the optimal alliance strategy; that is, how states can best configure military cooperation to create security through these partnerships. The dominant strategy anchors and constrains alliance design choices, forming a standard of security cooperation that, this book argues, all states recognize and most states adopt.
This dominant strategy alternates between two broad approaches. The first is a realpolitik approach marked by conditional commitments, limited institutionalization, narrow scope, and occasionally “predatory” features like the division of spoils. Alliances serve limited, short-term functions, with realignment and abandonment not merely expected but even valued to prevent concentrations of power and maintain stability.
By contrast, the second is an integrative approach to security cooperation. Under this strategy, alliances define long-term, even indefinite, patterns of military relations among members. They feature coordinating mechanisms with wide policy scope, using tighter coordination—rather than realignment—to adapt the pact to emerging challenges. This coordination can be extensive, even intrusive, touching upon the states’ core security prerogatives, such as integrating military commands; delegating decision-making on troop training and deployment; harmonizing intra-allied production and financing of equipment; and encompassing broader economic, political, and social exchange. Under this approach, alliances constitute the institutional foundation for robust policy relationships and security communities.
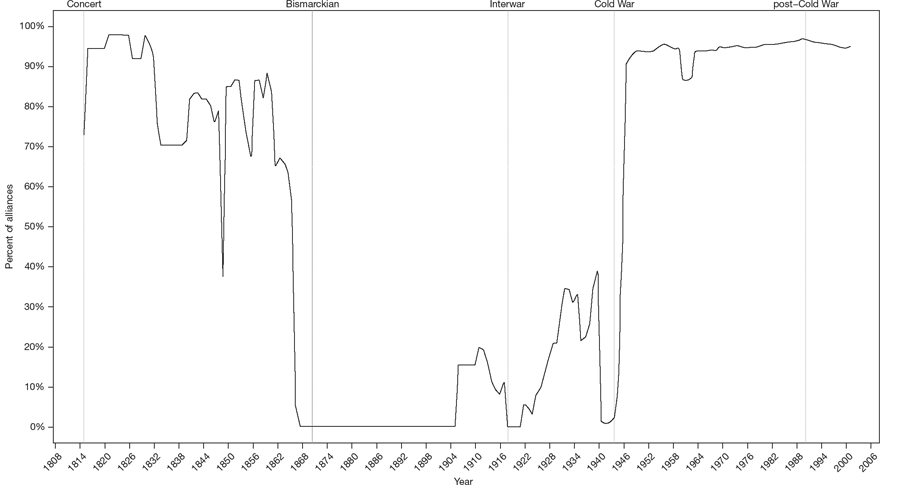
The dominant alliance form’s exact features vary by time period, but the Utrecht (1715–55), Bismarckian (1873–94), and Interwar (1919–38) eras followed the realpolitik approach. An integrative dominant strategy prevailed in the Concert (1815–66), Cold War (1946–91), and post–Cold War (1992+) periods. We can use the Alliance Treaty Observations and Provisions (ATOP) dataset to visualize and formalize these patterns from 1815–2003.14 The graphs below present the proportion of alliances featuring a particular characteristic.15 The alternation between realpolitik and integrative strategies is most pronounced with general coordinating bodies: alliance bodies with the delegated, decision-making authority to manage and coordinate intra-allied policy and military planning and operations, often through a permanently seconded bureaucracy. As seen in figure 1.1, 80.66 percent of alliances had a formal organization in the Concert period. After the Franco-Prussian War of 1870–71, no pacts possessed such bodies until 1907. After World War II, this feature’s prevalence suddenly spikes from 8.99 percent in 1946 to 90.64 percent in 1948 and is even higher today. Figure 1.1 displays proportions, so even as the number of states and alliances increase by orders of magnitude, few go against the dominant alliance strategy, whether realpolitik or integrative.
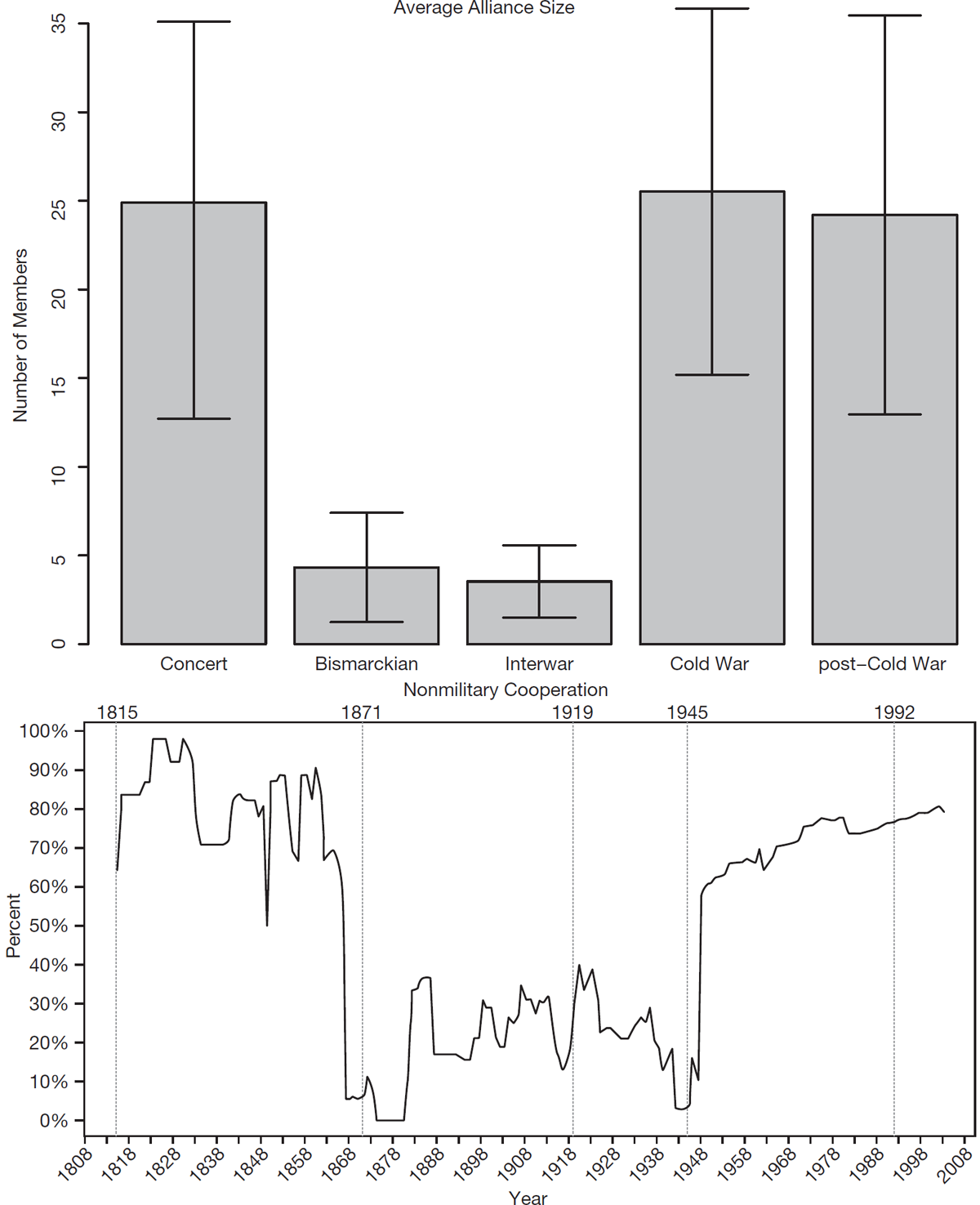
This pattern applies to more than a dozen other institutional features. Integrative alliance strategies aim to create robust, overlapping intra-allied cooperation. Periods with an integrative dominant form should therefore see disproportionately higher levels of mediation/arbitration mechanisms to settle internal disputes, as well as cooperation on nonmilitary policy issues. Because of this, following Wallander and Keohane (1999), these pacts should often have more members and survive longer. Moreover, we should expect sharp drops in these features’ prevalence during realpolitik eras, which manage policy spillover and externalities differently.
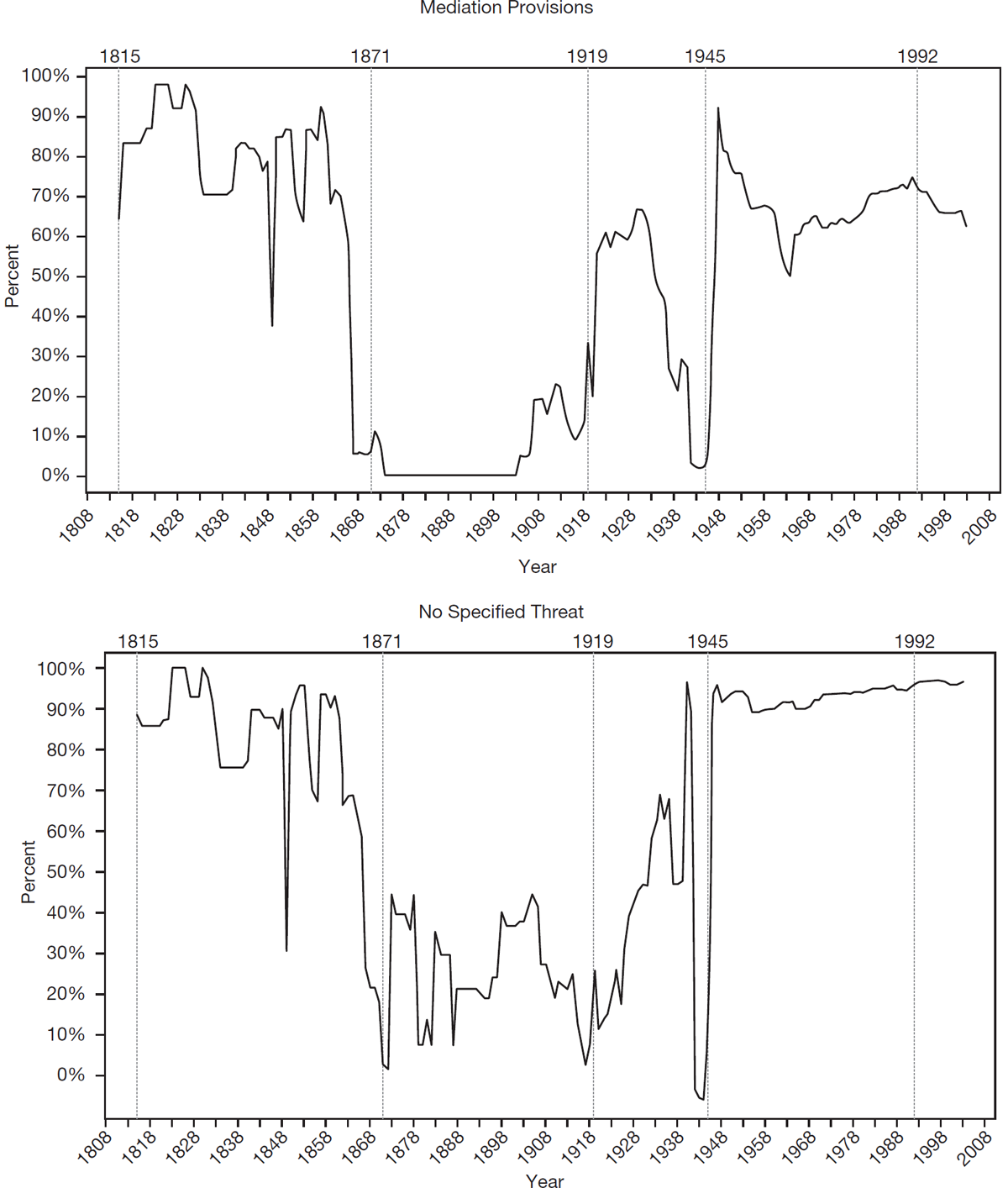
And that is what we see in figure 1.2. With alliance size, for example, most partnerships had a dozen members or more during the early 1800s and again after 1945. During the realpolitik eras, they had three on average. Cooperation on nonmilitary issues was similarly prevalent during eras with an integrative dominant form, but only 11.16 percent of alliances had them outside of those years. Provisions for internal mediation were far more common outside the Bismarckian and Interwar periods than within them. Similarly, collective security pacts—those alliances not directed at specific targets (at least nominally) but instead concerned with any disturbance of the peace—are much more frequent during the Concert period and following World War II. In addition, since 1947, a majority of alliances have not specified an end date. Members expect their pacts to structure their security relations indefinitely. Prior to that year, fewer than one percent of alliances made a similar pledge. In total, integrative features—coordinating organizations, mediation provisions, nonmilitary cooperation, etc.—prevailed and disappeared as a block, seemingly as part of a single, underlying alliance strategy defining the interstate security system.
Similarly, the “predatory” features often found in realpolitik alliance strategies were disproportionately common during the Utrecht, Bismarckian, and Interwar years.16 Secrecy was common during the Utrecht period, and, as mentioned, nearly all pacts were covert during the Bismarckian era.17 However, this feature declined precipitously after World War I, as seen in figure 1.3. Asymmetric obligations (rather than mutual effort for collective security) and articles detailing the division of gains were similarly common in all three eras, with the Utrecht years in particular sanctioning territorial acquisition and changes to state boundaries.18 Moreover, as seen in figure 1.4, neutrality and offensive guarantees—typically used by partners to carve out separate spheres of influence and conquer territory, respectively—were found in just over half of alliances from 1871–1939. Notably, no pacts included a neutrality commitment prior to 1856, and only 1.46 percent have featured such a commitment after World War II. Finally, realpolitik strategies emphasize fluid rebalancing. Unsurprisingly, alliance failure and abandonment regularly occurred in periods following that dominant form, while only 3.89 percent of alliances collapsed outside of such periods.
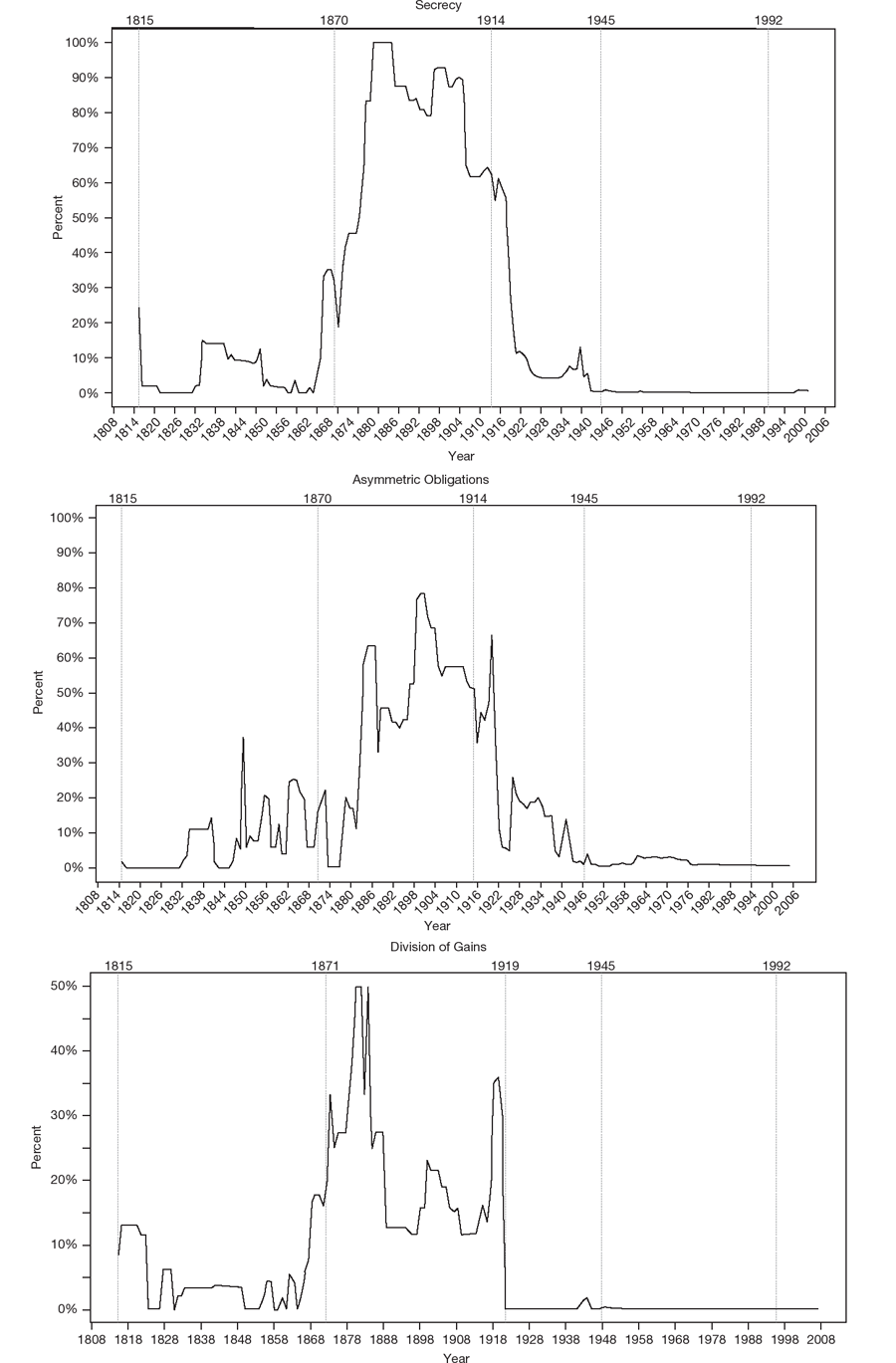
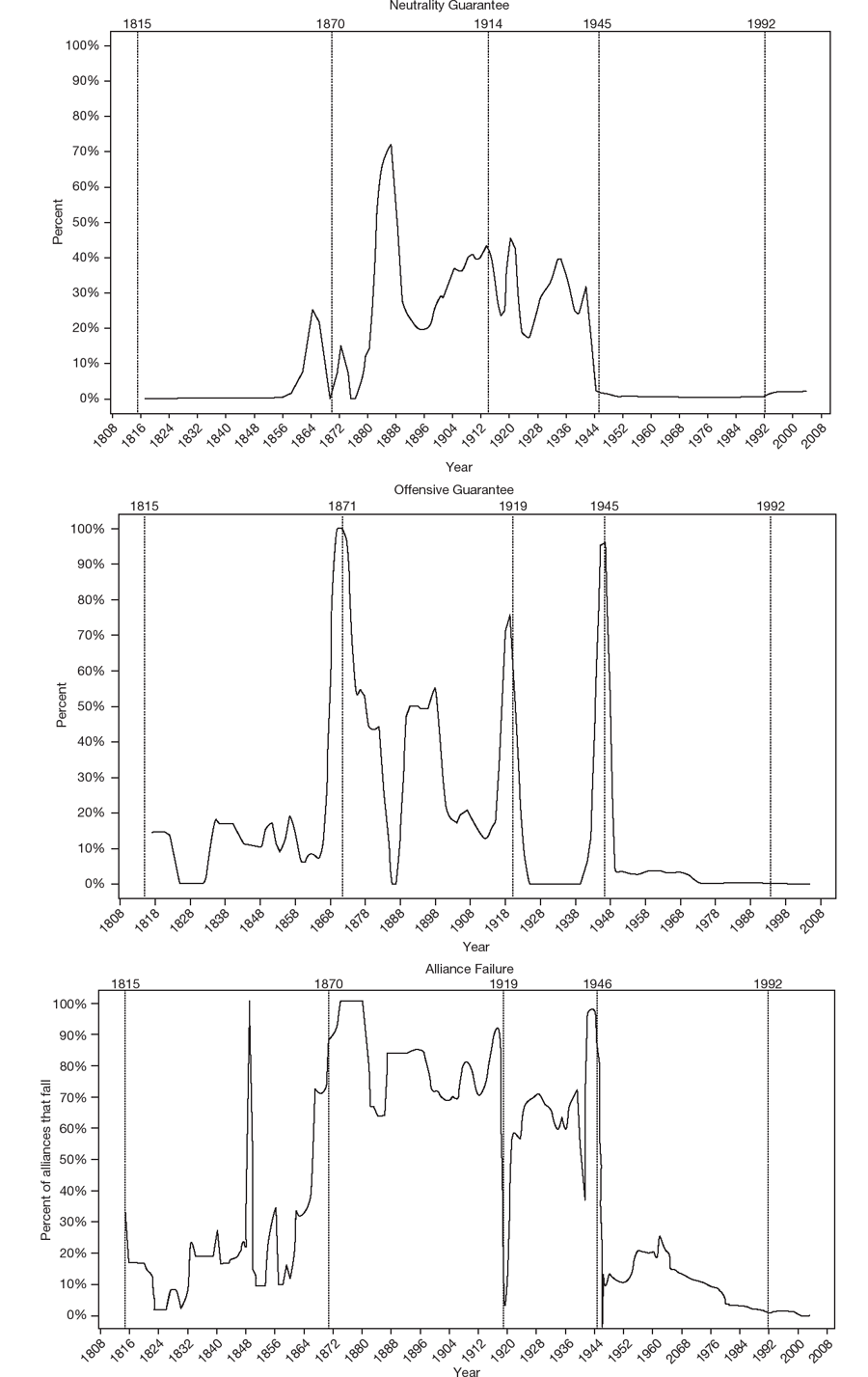
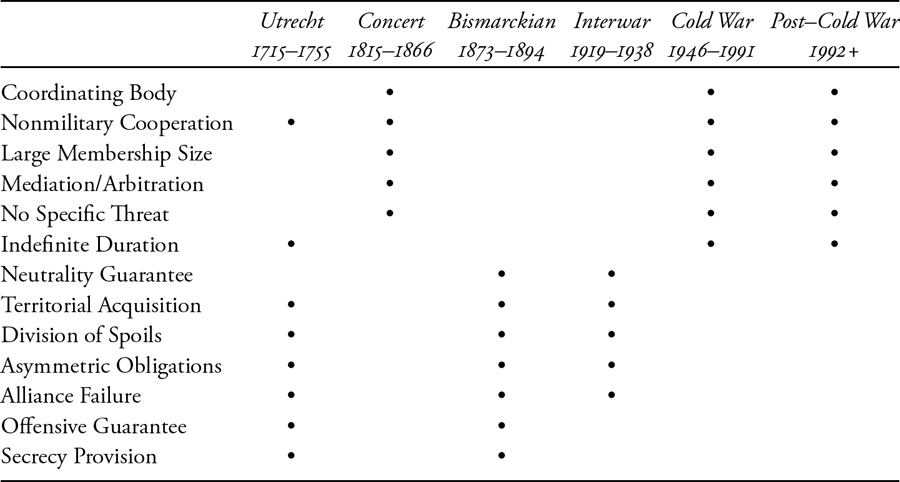
These and additional patterns are summarized in table 1.1, which marks whether an alliance feature disproportionately appears in a particular period. From the preceding analysis, we can make several claims about the dominant alliance form. First, to reiterate, it broadly alternates between a realpolitik approach and an integrative one. Military pacts during the Utrecht, Bismarckian, and Interwar periods generally had narrower and shallower provisions. They organized military—and only military—expectations among small groups of states, typically through individuated obligations and contributions. Pacts were loose, almost informal arrangements, possessing few management or coordination mechanisms. Alliance failure and abrogation was also significantly more likely during these years. Finally, the institutional features suggest a more “predatory” approach to foreign strategy, with secrecy, neutrality, territorial acquisition, and the division of spoils featured prominently in treaties.
By contrast, an integrative dominant alliance strategy characterizes the Concert period and post–World War II global system. Alliances possessed broader and deeper features, deliberately incorporating diplomatic, political, economic, and even social coordination into their military discussions. NATO, for example, called for divisions of labor in military production as well as cooperation on democratic governance and development. The Rio Pact established permanent committees on human rights, international law, and economic development, ranging well beyond traditional defense concerns. Membership is significantly larger than during the realpolitik eras, and pacts committed their members to multiple, overlapping obligations through formal, robust deliberative mechanisms. Overall, the dominant alliance strategy during these years pursued a “stabilizing” or “institutional adaptation” approach to foreign strategy, managing threats, externalities, and spillover through increased coordination.19 We see much less alliance defection.
Second, major wars clearly play a critical role in destroying the previous dominant form and fostering a new one. They demarcate sharp disjunctures in the prevalence of alliance obligations, producing noticeable “peaks” and “valleys” in the graphs. Integrative dominant strategies suddenly shift to realpolitik ones, and vice versa, around these conflicts. The winners often create wartime networks that carry into the peace, while the losers see their partnerships shattered. Consequently, any theory of the dominant strategy must account for these wars.
Third, within the periods initiated and bracketed by major wars, the sheer prevalence of the dominant form’s features is striking. Most countries converge on their period’s prevailing alliance strategy. Just as important, very few adopt alternative designs. As mentioned, these strategies are beliefs connecting institutional means to security ends through alliances. Given the prevalence and pervasiveness of the dominant strategy despite geographic and historical variation, as well as the steadily increasing number of states, it is unlikely that this form is the product of “rational” means-ends calculation. Instead, judged by its systemic effects on alliance design, this strategy approaches an injunctive norm, attaining a “unique conceivability” that effective alliances must look and behave a certain way.20
We might ask, for example, why Bismarckian and Interwar alliances did not use institutional binding, costly signaling, organizational sunk costs, or other mechanisms to improve reliability, when so many pacts during these years failed and states repeatedly suffered abandonment. Why rely instead on continual realignment, sometimes to partners that had just reneged? Schroeder offers a clue, writing: “Alliance flexibility of this sort was not merely considered normal, so that statesmen, when concluding alliances, regularly tried to calculate at what point their ally was likely to defect, but was even considered to a degree necessary, as one means of maintaining an overall balance.”21 Indeed, the Utrecht treaties explicitly aimed “to settle and establish the peace and tranquility of Christendom by an equal balance of power (which is the best and most solid foundation of a mutual friendship, and of a concord which will be lasting on all sides).”22 Of course, the Arab League and NATO members aimed at similar objectives, seeking in the latter’s case to “reaffirm their faith in the purposes and principles of the Charter of the United Nations and their desire to live in peace with all peoples and all governments.” Yet they approach these goals through markedly different alliance strategies. The previous graphs and analysis suggest a social process drives states toward institutional isomorphism and strategic emulation in their military pacts within periods, but divergence across them.
Finally, the dominant alliance strategy is intimately connected to questions of international order, specifically on security. Ikenberry defines order as the “governing” arrangements among states: “The focus is on the explicit principles, rules, and institutions that define the core relationships between the states that are party to the order. This limits the concept of order to settled arrangements between states that define their relationship to each other and mutual expectations about their ongoing interaction.”23 Convergence on a single alliance strategy constitutes an integral part of this order, as all states can evaluate military relations against a common standard, even if they depart from the dominant form. This produces not only common expectations over security behavior, but even beliefs about what functions alliances serve and how they produce international stability.
Further, as detailed in the next chapter, the dominant form emerges from major war and the hegemon’s subsequent alliance decisions, mirroring theories explaining the creation and character of international orders. Far more structure emerges from these conflicts than we have realized. But where those studies focus almost exclusively on great or rising powers, the dominant strategy’s prevalence suggests a different question: How does order spread? Something causes secondary and peripheral countries to ignore their individuated circumstances and to accept and enact a specific belief about how alliances can create security effectively. This belief potentially constrains the great powers, preventing them from adapting their pacts even as strategic conditions change. How can we explain the emergence, diffusion, and change of dominant alliance strategies?
The existing literature on alliances and international security offers two possible answers to this question: common threats and hegemonic imposition. It also provides a third approach, rational institutionalism, which serves as this book’s primary foil. Each rests on a functionalist approach to institutional design—that states select features based on means-ends calculations to maximize security generation and/or resolve problems preventing alliance cooperation. Unfortunately, they provide little analytical traction in explaining the dominant strategy.
Both common threats and hegemonic imposition can explicitly incorporate a role for great power war. The former contends that alliance isomorphism stems from shared external security challenges across military pacts. Major wars could orient most countries against a common state or political threat, much as the Concert system gathered the European great powers against domestic democratic movements. Alliances adopt the same strategies to deal with the same challenges, producing a dominant form.
We have strong reasons to question this approach. Holsti (1991) finds that the drivers of interstate conflict (1648–1989) have diversified over time. Whereas territorial disputes caused 34 percent of conflicts between 1648 and 1714, this issue appeared in only 15 percent during the Cold War. Issues like protecting citizens residing abroad or defending commercial interests have taken its place. If Holsti is correct, we should see increasing diversity in alliance strategy over time. But in fact, the dominant form is generally stable and prevalent within historical eras and sharply divergent across them.
Even if most states faced a similar threat, they are likely to possess different internal constraints or vulnerabilities, leading to divergent preferences over alliance strategy. Even when broad shifts in members’ domestic characteristics occur, they do not lead to the expected patterns in pact design. The hierarchy and small states literatures, for example, expect asymmetric alliances. Decolonization and post–Cold War fragmentation have increased the number of small states, but asymmetry has actually declined. Similarly, the enhanced reliability of democracies might obviate organizational sunk costs. But military pacts have arguably increased their formalization and institutionalization following the second and third waves of democratization.24
A related, power-based approach draws from hegemonic stability theory. Keohane (1984) discusses the hegemon’s role in establishing and maintaining international economic regimes, while Ikenberry (2001) makes a similar argument with regard to security orders. Hegemons could produce a dominant form by imposing their preferred alliance strategy over much of the interstate system.
But this approach also confronts multiple problems. Using ATOP, no state participates in more than 15.4 percent of alliances in any given period, making it unlikely that even the most powerful hegemons are directly proliferating the core alliance’s design. Furthermore, the dominant strategy gains similar prevalence regardless of system polarity. Indeed, we might expect multipolar systems especially to feature several dominant forms, as multiple powerful states impose their preferred designs on clients. But countries during the multipolar Concert and Bismarckian eras still converged on singular alliance strategies. Moreover, despite having some of the same great powers, regime types, and even in some cases leaders, those two periods produced different dominant forms, the integrative Congress system and Bismarckian realpolitik.
In addition, peripheral states—those wholly unconnected to the great powers through alliance ties—also converge on the dominant strategy. The Arab League, the Economic Community of West African States (ECOWAS), and other regional security organizations deliberately excluded major countries from their local consolidation processes and security discussions. That they nevertheless adopt the same alliance features—without great power interest, despite significantly reduced capabilities, and often confronting different security challenges—only reinforces this book’s puzzle.
Finally, to this point, the book has implicitly treated rational institutionalism as a theoretical foil. It now does so explicitly. Following Koremenos et al. (2001) and Koremenos (2016), states are functionalist utility maximizers, picking organizational features to solve specific cooperation problems and achieve goals. Formalization and reputation costs can overcome credibility deficits.25 Decision-making bodies can manage policy interdependence and spillover.26 Information sharing can constrain members and mitigate moral hazard, or the alliance can use conditional obligations and ambiguous promises to the same effect.27 This framework takes institutional design seriously, providing particularist explanations linking complex and diverse organizational features—flexibility, centralization, scope, control—to multiple system and state-level variables. Koremenos et al. (2001) includes sixteen separate conjectures on institutional design, while Koremenos (2016) and the studies above add even more.
As such, rational institutionalism is constitutionally ill-suited to explain transhistorical uniformity, not variation. Even if major wars generate a widespread and common cooperation problem, countries should still adapt their alliance strategies to individual (e.g., bad reputations, regime type) and relational (e.g., asymmetric power, interdependence) conditions. We should still see some organizational variation, particularly as the number and diversity of states increase.28 Similarly, this approach has difficulty accounting for systemic “nonevents.” As noted, the Utrecht, Bismarckian, and Interwar systems saw frequent alliance defection. Major wars could have created pervasive credibility problems. But why did states fail to create institutional solutions—organizational sunk costs, arbitration mechanisms, management councils—to address widespread abrogation, as rational design would predict? Why did institutionalization not occur as a utility-maximizing response?
Focused on diversity, institutionalism cannot provide a consistent or comprehensive explanation for the dominant strategy. But its logic remains inherently compelling. We expect states to tailor their strategies, especially given the complexity and interdependence of foreign policy. Indeed, rational institutionalism’s inability to explain the absence of diversity in alliance strategy animates the central puzzle. Consequently, institutionalism acts as this book’s foil. The following chapter’s theory claims that the dominant form emerges from a social process of legitimacy and standard setting. The empirical analysis will directly contrast this approach with institutionalism’s expectations regarding utility maximization and organizational tailoring.
The following chapter provides a social theory of strategic convergence. It draws upon network analysis, as well as sociological approaches to rank and status, to develop two causal mechanisms—credibility and status diffusion—to explain how the dominant form emerges from major wars and spreads throughout the interstate system, structuring alliance and security relations for decades. The chapter outlines testable hypotheses that distinguish these causal pathways from the alternative explanations and rational institutionalism.
Chapters 3–7 evaluate those hypotheses using quantitative analysis, historical and archival case studies, and elite interviews. Chapter 3 uses statistical evidence to establish that states and alliances do indeed copy the core pact’s design. It presents seven separate tests verifying both mechanisms, as well as general implications from the theory. The central partnership drives the overall pattern of alliance strategy and design we see historically, with secondary and peripheral countries leading this process.
With this general pattern set, the book uses qualitative analysis to test the theory’s microfoundations. A state’s position in the alliance network determines which mechanism it uses for emulation. Primary countries (i.e., core alliance members) and secondary ones worry about relative reliability and follow the credibility diffusion mechanism. Peripheral states emulate to seek status through the normative diffusion process. Chapters 4–6 examine each state type sequentially (i.e., primary, secondary, peripheral), ensuring that the theory holds at all network positions. The first case, in chapter 4, explores alliances between the three, late-nineteenth-century conservative empires: Germany, Austria-Hungary, and Russia. Following its victory in the Franco-Prussian War (1871), the newly declared German empire founded its central military pact with Austria-Hungary, the Dual Alliance (1879). It then used this body to launch further partnerships with Russia, creating a solid conservative political bloc in Europe and preventing Franco-Russian reconciliation. These three countries repeatedly concluded military agreements with one other, and the agreements repeatedly failed. Austria-Hungary—the weakest of these three great powers—refused to allow its partners to exceed the Dual Alliance’s terms in any subsequent pact. This case highlights how issues of credibility and standard-setting constrain even the most powerful states in the system.
Next, chapter 5 examines NATO, an integrative core alliance, and its effect on two secondary, Cold War partnerships: the Manila Pact (aka the Southeast Asia Treaty Organization or SEATO, signed in 1954) and the Baghdad Pact (aka the Central Treaty Organization or CENTO, signed in 1955). The rising Soviet threat prompted the United States to establish a network of alliances containing Russia. While NATO anchored Europe, SEATO and CENTO managed Southeast Asia and the “northern tier” of Middle Eastern / Central Asian countries (stretching along the USSR’s southern border), respectively. During negotiations, regional SEATO and CENTO members consistently upheld NATO as the standard of political credibility, demanding that Washington upgrade its military and institutional commitments to match those found in the North Atlantic Alliance. The United States instead offered arms transfers, financial assistance, and training packages that in some cases exceeded what it provided to European partners. Nevertheless, secondary countries rejected these measures, doubting American commitment when Washington refused to close the institutional and strategic gap between NATO and their pacts.
Chapter 6 presents a final case assessing peripheral countries in southern Africa. The Southern Africa Development Community (SADC) established two security bodies after the Cold War: the Organ on Politics, Defence, and Security (OPDS or the Organ, launched in 1996) and the Mutual Defence Pact (2003). Unlike the two previous cases, status-seeking behavior drove emulation here. In particular, South Africa and Zimbabwe seized upon Western models of alliance strategy as they fought to legitimize their organizational leadership. Despite substantial differences in NATO and SADC’s military challenges, as well as SADC members’ limited ability to fund and staff their security organizations, these partners nevertheless settled upon a design emulating the North Atlantic Alliance.
A final empirical chapter examines the dominant strategy’s effects. The theory implies that emulative partnerships should fail less often than nonemulative ones, as states converge on the dominant strategy for either credibility or status benefits. Chapter 7 returns to statistical modeling to find that dominant alliances are significantly less likely to collapse. The more pervasive the dominant form (whether integrative or realpolitik), the more stable and cohesive the interstate security system.
This carries important policy implications, and the theory more generally contributes to several scholarly literatures. The concluding chapter examines how the dominant strategy and this book’s mechanisms enhance our understanding of international order. In particular, it discusses the challenges to adopting a more transactional approach to American foreign policy. The book’s transhistorical framework allows us to directly compare the effects of integrative versus realpolitik alliance strategies. The credibility diffusion mechanism especially demonstrates that transactional approaches are significantly more challenging to manage, less durable, and entail much wider network costs than proponents acknowledge.
Finally, the book ends with a central policy recommendation. Asia is the locus of future strategic competition and global economic dynamism. A rising and more assertive China presents the United States with a complicated and multidimensional challenge. Yet the region possesses few institutions to manage this confrontation, and even fewer that can successfully coordinate military policy to escalating Chinese territorial claims and belligerence. Despite both the George W. Bush and Obama administrations reorienting America’s strategic focus toward Asia, local leaders still worry that they will be overshadowed by US interests in Europe and the Middle East. In short, they worry about relative reliability. The book’s theory suggests that only a completely emulative alliance—a true “NATO in Asia”—will demonstrate American prioritization of and commitment to this region.
1. These treaties can be found in Gibler 2008.
2. Ideas discussed in this chapter, as well as in chapters 2 and 4, have been explored in Kuo 2019.
3. Leeds et al. 2002, 238.
4. Waltz 1979; Walt 1987.
5. Snyder 1997.
6. Mattes 2012; Crescenzi et al. 2012; Fearon 1997.
7. Handel 1990; Vital 1982; Job 1992; Sylvan and Majeski 2009; Gasiorowski 1991.
8. Thies 2003.
9. Lipson 1991.
10. Fearon 1994; Siverson and King 1980.
11. Singer and Small 1966; Levy 1981; Siverson and King 1980; Kegley 1994; Wayman 1984; Midlarsky 1983, 1986.
12. Benson 2012; Kim 2011; Frost-Nielsen 2017.
13. Bensahel 2007; Bearce et al. 2006.
14. Leeds et al. 2002. Schroeder (1994) comprehensively analyzes the preceding Utrecht period.
15. More formally, the unit of observation is the nondirected alliance dyad, as further detailed in chapter 3.
16. ATOP does not contain data on the Utrecht period. Claims about those years instead come from handcoded analysis of Gibler 2008.
17. The secrecy graph is drawn from Kuo 2019.
18. Further, many alliances in the Utrecht period included provisions for nonmilitary cooperation and defined contributions. While these outwardly appear as integrative features, they were understood differently than today. Nonmilitary cooperation referred then to issues of succession and inheritance, with monarchs specifying lineage orders and, by extension, what territory nations gained. When modern alliances define contributions, they typically make general commitments to divide costs equally. The Arab League, for example, directs a Permanent Military Commission to discuss what contributions each member can provide. By contrast, Utrecht alliances specified the exact number, type, nationality (to exclude mercenaries), and even command structure and officers that each country would supply.
19. Leeds and Mattes 2007.
20. Taylor 1984.
21. Schroeder 1994, 7.
22. Article II, Peace and Friendship Treaty of Utrecht between Spain and Great Britain, https://en.wikisource.org/wiki/Peace_and_Friendship_Treaty_of_Utrecht_between_Spain_and_Great_Britain.
23. Ikenberry 2001, 23.
24. Huntington 1991; Gunitsky 2017.
25. Lipson 1991; Morrow 2000; Fearon 1997; Mattes 2012.
26. Wallander and Keohane 1999; Wallander 2000.
27. Benson 2012; Kim 2011.
28. Crescenzi et al. 2012; Siverson and Starr 1994; Leeds 2003; Lake 2009; Wallander and Keohane 1999.